Just for the record. They are old, they are good, but they are end of life and we don’t use them any more.
Tag Archives: Cisco
Cisco ASA and lot of email recipients
Those days we faced the problem that we recived a mail with approx 150 recipients.
Somewhere in the communication it seams that a mail address is broken by the asa.
On the Outside of the ASA you see following in the trace:
Inside E-Mail Server (Blue) mail.example.com
Outside E-Mail Server (Red) mail.asdf.com
220-mail.example.com ESMTP Server [Wed, 18 Aug 2010 10:30:58 +0200]
220-Ready to recycle your bits, but we don't want
220 your unsolicited or bulk e-mail (ie: spam)
EHLO mail.asdf.com
250-mail.example.com Hello mail.asdf.com [192.168.0.1]
250-SIZE 4194304
250-PIPELINING
250-AUTH PLAIN LOGIN CRAM-MD5 NTLM
250-STARTTLS
250 HELP
MAIL FROM:<asdf@asdf.com> SIZE=42157
RCPT TO:<user1@example.com>
<output omited>
RCPT TO:<user20@example.com>
RCPT TO:<user21@
250 OK
example.com>
RCPT TO:<user22@example.com>
RCPT TO:<user23@example.com>
RCPT TO:<user24@example.com>
<output omited>
250 Accepted
<output omited>
250 Accepted
501 <user21@XXXXXXXXXXXXXX: '>' missing at end of address
250 Accepted
250 Accepted
250 Accepted
On the Inside of the ASA you see following in the trace:
Inside E-Mail Server (Blue) mail.example.com
Outside E-Mail Server (Red) mail.asdf.com
220-mail.example.com ESMTP Server [Wed, 18 Aug 2010 10:30:58 +0200]
220-Ready to recycle your bits, but we don't want
220 your unsolicited or bulk e-mail (ie: spam)
EHLO mail.asdf.com
250-mail.example.com Hello mail.asdf.com [192.168.0.1]
250-SIZE 4194304
250-PIPELINING
250-AUTH PLAIN LOGIN CRAM-MD5 NTLM
250-STARTTLS
250 HELP
MAIL FROM:<asdf@asdf.com> SIZE=42157
RCPT TO:<user1@example.com>
<output omited>
RCPT TO:<user20@example.com>
RCPT TO:<user21@ 250 OK
XXXXXXXXXXXXXX
RCPT TO:<user22@example.com>
RCPT TO:<user23@example.com>
RCPT TO:<user24@example.com>
<output omited>
250 Accepted
<output omited>
250 Accepted
501 <user21@XXXXXXXXXXXXXX: '>' missing at end of address
250 Accepted
250 Accepted
250 Accepted
This is a little bit strange so i will ask the Guys from Cisco if this is a known feature or a bug.
For the Momemt we have disabled the esmtp fixup, on monday we will do future analysis.
If you feel this helps a bit or may be not ? Please leave a comment.
Cisco ASA and SMTP
We recently bought so new Firewalls to replace to aged Cisco PIX515e with some new Gear. We decided to use Ciscos new Firewall flagship the Cisco ASA Devices. Everything was fine after the replacement, we transfered the configuration from the old boxes to the new with the help of the Cisco Security Manager.
Later that day there was complains about e-mails are not delivered properly.
On the Cisco PIX with Software 6.2 we had implemented following:
no fixup smtp
For the ASA5510 we had to implement following
policy-map type inspect esmtp esmtp_pmap
parameters
allow-tls action log
policy-map global_policy
class inspection_default
no inspect esmtp
inspect esmtp esmtp_pmap
exit
exit
If you feel this helps a bit or may be not ? Please leave a comment.
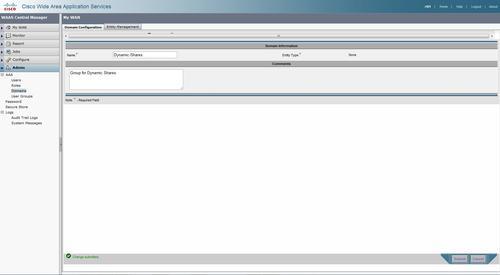
Access-based Enumeration (ABE) and Cisco WAAS
Access-based Enumeration (ABE) is a smart feature to let users see only the folders they have access to.
But if you have Cisco WAAS deployed in your network please be aware you have to add a Dynamic share to the waas configuration so the waas knows about this.
—– EDIT BEGIN —–
2010-09-17 We found out the Hardway you have to add the System to the AD. So i will show the Story in a new Post:-) Stay tuned, guys.
—– EDIT END ——-
Cisco Wide Area Application Services Configuration Guide (Software Version 4.1.7)
Step 1
For creating a dynamic share you have to add a Domain to the Cental Manager eg “Dynamic Shares”
Step 2
Create a entry under the dynamic shares in the global configuration.
On the WAE CLI
ToBe Done
If you feel this helps a bit or may be not ? Please leave a comment.
Cisco MDS 9222i with ACS
If you want to configure tacacs+ on the Cisoc MDS9222i Series you have to enable first the feature.
[sourcecode autolinks=”false” gutter=”false”]
feature tacacs+
[/sourcecode]
After this the commands to configure the Tacacs+ are available.
[sourcecode autolinks=”false” gutter=”false”]
feature tacacs+
!
tacacs+ distribute
tacacs-server timeout 10
tacacs-server host 10.0.243.247 key 0 secertkey
tacacs-server host 10.0.243.248 key 0 secretkey
tacacs+ commit
!
aaa group server tacacs+ AAA-Servers
server 10.0.243.247
server 10.0.243.248
deadtime 5
!
aaa authentication login default group AAA-Servers
aaa authentication login console local
aaa authentication login error-enable
!
ip route 10.0.243.247 255.255.255.255 10.0.160.1 interface mgmt0
ip route 10.0.243.248 255.255.255.255 10.0.160.1 interface mgmt0
!
interface mgmt0
ip address 10.0.160.99 255.255.255.0
switchport description Management
switchport speed 100
[/sourcecode]
On the ACS side you have to configure the shell profile with the following role:
[sourcecode autolinks=”false” gutter=”false”]
shell:roles="network-admin"
[/sourcecode]
If you feel this helps a bit or may be not ? Please leave a comment.
Cisco WAAS and Tacacs+
Configuration with the Central Manager
tacacs key **** tacacs host 10.0.243.247 primary tacacs host 10.0.243.248 tacacs key **** authentication login local enable secondary authentication login tacacs enable primary authentication configuration local enable secondary authentication configuration tacacs enable primary authentication fail-over server-unreachable aaa authorization commands 15 default tacacs+

WAVE-276 and the second Virtuale Blade
So finally with WAAS-4.1.3.55 cames out and you can conifigure a second virtual Blade.
Nice;-)
DMVPN with Linux
I know since i discovered the DMVPN in 2004/5 this is a very intelligent combination of IPsec, GRE and NHRP. Many Thanks to the Guys at Cisco, Christoph, Frederick and all other.
This week i discovered “opennhrp” on sourceforge.
It took me a minute or two to have a VM with debian up and the needed tools installed.
I used VMWare with a bridged ethernet interface for testing, installed debian 4.0 netinstall iso and upgraded to sid / testing, so i got Kernel Version 2.6.26-1-686.
Then downloaded ipsec-tools-0.8-alpha20090126.tar.bz2 from the site. you have to install some libs and tools to build ipsec tools, like kernel headers and so on:-) and done some configure and make stuff.
I went to make opennhrp, well all done with out a problem to here.
Next i configured racoon and ipsec-tools and opennhrp like this:
/etc/ipsec-tools.conf #!/usr/sbin/setkey -f spdflush; spdadd 0.0.0.0/0 0.0.0.0/0 gre -P out ipsec esp/transport//require; spdadd 0.0.0.0/0 0.0.0.0/0 gre -P in ipsec esp/transport//require;
/etc/racoon/racoon.conf
path pre_shared_key "/etc/racoon/psk.txt";
remote anonymous {
exchange_mode main,aggressive;
lifetime time 24 hour;
# nat_traversal on;
script "/etc/opennhrp/racoon-ph1down.sh" phase1_down;
proposal {
encryption_algorithm 3des;
hash_algorithm sha1;
authentication_method pre_shared_key;
dh_group 5;
}
}
sainfo anonymous {
lifetime time 12 hour;
encryption_algorithm 3des, blowfish 448, rijndael;
authentication_algorithm hmac_sha1, hmac_md5;
compression_algorithm deflate;
}
/etc/racoon/psk.txt 10.2.0.90 1234
/etc/opennhrp/opennhrp.conf
interface gre1
map 172.255.255.1/24 10.2.0.90 register cisco
cisco-authentication 1234
shortcut
No get the Tunnel UP:
ip tunnel add gre1 mode gre key 1234 ttl 64 ip addr add 172.255.255.2/24 dev gre1 ip tunnel change gre1 local 10.0.81.115 ip link set gre1 up
Now its time to get on the other side.
We are using a Cisco 1812 with c181x-advsecurityk9-mz.124-15.T7.bin running.
crypto isakmp policy 10
encr 3des
authentication pre-share
group 5
!
crypto isakmp key 1234 address 0.0.0.0 0.0.0.0
!
crypto ipsec transform-set TRANSFORMSET_3 esp-3des esp-sha-hmac
mode transport
!
crypto ipsec profile Profile3
set transform-set TRANSFORMSET_3
!
interface Tunnel888
ip address 172.255.255.1 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
ip mtu 1400
ip flow ingress
ip nhrp authentication 1234
ip nhrp map multicast dynamic
ip nhrp network-id 10064
ip nhrp holdtime 360
ip nhrp max-send 200 every 10
ip route-cache same-interface
ip tcp adjust-mss 1350
load-interval 30
tunnel source 10.2.0.90
tunnel mode gre multipoint
tunnel key 1234
tunnel protection ipsec profile Profile3
and viola
Router# sh dmvpn interface tunnel 888 Load for five secs: 8%/3%; one minute: 9%; five minutes: 10% Time source is NTP, 22:14:22.148 CET Sat Feb 14 2009 Legend: Attrb --> S - Static, D - Dynamic, I - Incompletea N - NATed, L - Local, X - No Socket # Ent --> Number of NHRP entries with same NBMA peer Tunnel888, Type:Hub, NHRP Peers:1, # Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb ----- --------------- --------------- ----- -------- ----- 1 10.0.81.115 172.255.255.2 UP never D
Router# ping 172.255.255.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.255.255.2, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 4/4/8 ms
this looks great:-)
Many thanks Timo for doing such a impressiv work. I like the cisco for they impressiv boxes and i also like opensource software.
— edit February 15, 2009 at 12:09 am —
I found after a while no packets traveling, the nhrp registration had gone on the cisco side may be holdtimers differ so added “holding-time 360” to the opennhrp.conf , a opennhrpctl purge fixed the problem.